**UPDATE 10/31/18**
Since I made this original post, Microsoft has made attempts to consolidate the enrollment portals for Azure MFA as well as Azure Self-Service Password Reset. This could be accessed through a portal at https://aka.ms/setupsecurityinfo, but at the time of writing this (and for the last several months) this site has been down. Regardless, you can instead now go to https://aka.ms/setupmfa to directly access the MFA enrollment portal instead of following the procedure I had originally posted. If you want to provide a more customized experience, the original procedure may still be useful to you.
**END UPDATE***
Azure MFA is a great service that adds an additional layer of security to user authentication, but one common complaint when enabling the feature is the inability to have users pre-configure their settings.

Pre-enrolling in MFA has been something that is always asked about but unfortunately enrollment is prompted when the first MFA challenge is required for authentication. It would seem like a simple feature change to enable users to enroll before they are required to use MFA, but Microsoft has not introduced this yet for the cloud-only version of Azure MFA (not using the on-premises MFA Server as this does have a portal).
Therefore, we need a workaround. We simply need to create a scenario where MFA is required for authentication, but not for a service or resource that the user needs immediate access to. With Conditional Access based MFA, we can easily do this.
Note that there are two methods for enabling Azure MFA: At the service-level using per-user MFA or through Conditional Access. In this case, we are assuming the service-level per-use MFA is not being used.
To do what we want, we need to create or use an application registered in Azure AD that provides no actual business value and create a Conditional Access policy scoped only to that application that requires MFA.
Deploy Dummy Web App
The target web application can be one that is already registered in Azure AD as a partner application (such as DropBox or SalesForce), but the downside to this would be that users would either be signing up for a cloud service using their corporate credentials or a subscription would be required.
Because we simple need an application in Azure that we can reference with a Conditional Access policy, we can easily create a dummy web app.
To do this, we need a server running Internet Information Services (IIS) to host a simple website for us, which can even be a single blank page. No need for this to be any corporate website or anything that is even connected to internal resources, it can be a web server isolated the rest of the network as long as it can have an outbound Internet connection.

Here, I've simply just setup a new site in IIS that has an internally signed SSL certificate. Using hostname binding, I am easily able to add this as a new website on an existing server by making my site respond specifically to https://mfaenrollsite.techmymind.com.
Now that I have a dummy site to use, I need to make it available in Azure AD. Instead of creating firewall rules, public DNS entries and potential routing configurations, I have opted to use that Azure AD App Proxy.
Create Azure AD App Proxy
The Azure AD App Proxy uses an on-premises connector that creates an outbound SSL connection to the Azure AD App Proxy service. This allows me to publish a web application to the Internet without any firewall rules to allow inbound traffic or DNS changes as all connectivity is established through the SSL (outbound) that was created by the connector.
This simply required the download and installation of the connector on my web server, but technically this connector could have lived anywhere as long as it could communicate via HTTPS to the web server. During installation, logging in using my O365 global admin credentials automatically associated the connector to my Azure AD.

Now that my dummy website can be accessed from the Internet, I need to make it available as an Azure AD Enterprise app to be used by Conditional Access.
Add Azure AD Enterprise App
When creating the Enterprise App in Azure AD I selected the option to use On-Premises Application as this assumes that the Azure AD App Proxy would be used to publish the app.

When configuring the App Proxy options, there are a couple directions I could have gone. Because the app proxy is a hosted service, I could use domain names for the app that Microsoft owns, which makes it easy for me as I do not have to create any DNS records or provide any SSL certificates as Microsoft does all this for me.
https://mfaenroll.techmymind.onmicrosoft.com
https://mfaenroll-techmymind.msapproxy.net
Alternatively, I can use my own custom domain, but this does require me to create a CNAME record to point my custom name to the Microsoft URL as well as provide a SSL certificate containing my custom name.
https://mfaenroll.techmymind.com
I chose to use my custom domain as I have an internally signed certificate to use. Note that my internal URL hostname does not need to be the same as my external URL hostname.

The other important option I have set here is for Pre-Authentication to use Azure Active Directory, which will cause Azure AD to perform the authentication and not rely on the web site's authentication controls... which in the case of my dummy app, there are none.
The other important thing I had to do was assign users to the Enterprise App. As with everything in Azure, the app must be scoped to individual users and/or groups. This included all my users that are planned to use MFA in the future.
Now that my app is in Azure AD, I can use it with Conditional Access.
Create Conditional Access Policy
A Conditional Access policy scoped to All Users (could be scope to only those who would be allowed to use MFA) and only my MFA Pre-Enrollment app that was created above.

This ensures that my policy only takes effect when trying to access my MFA Pre-Enrollment app and not any other Office 365 service or Enterprise App available in Azure. Therefore, this policy really will not affect any other service or application that may be required for my users to do their jobs.
The last configuration is to set the policy to Grant Access but require MFA. This is how the policy will call the Azure MFA service and therefore prompt the user to setup their MFA challenge settings the first time they access this app.

With the Conditional Access policy created and enabled, users can now use the app to enroll in their MFA settings before they are required to use them for any production service application.
Enrolling for MFA
At this point, my users can go and enroll their MFA challenge settings at their leisure. When they log into Office 365 or go to their MyApps (myapps.microsoft.com), they will now see the the MFA Pre-Enrollment application listed.

A custom icon for the app may make it look a little more appealing, but I just leveraged the default icon in the Enterprise App configuration.
Clicking on the MFA Pre-Enrollment app will redirect the user to the Azure AD authentication page, but since the user is already authenticated with a username and password, they are prompted to setup their MFA settings.
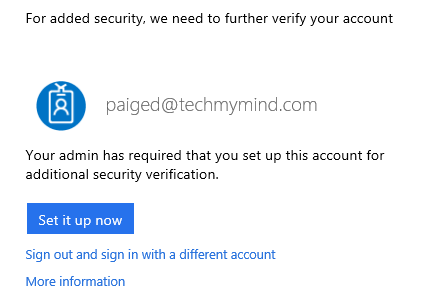
Once their MFA setup is complete, they are redirected to the actual MFA Pre-Enrollment dummy site that is running on my on-premises IIS web server. Here it may be relevant to provide some additional instructions or even some information pertaining to how and when MFA will be used. Anything can be provided here, but for my site, it's just a simple single-page.


Comments